Advertisement
What is a consensus algorithm?
For traditional structures, central agencies are the place to solve problems. That’s why the consensus of smaller departments is not an important issue. However, in the decentralized system (Blockchain), on the contrary, each small part (intersections) plays an important role. They are both the server that coordinates the operation of the system and the place to store important data. In order for the system to work smoothly, these intersections must exchange data with each other and establish consensus. That’s why blockchain consensus algorithms were born.
A consensus algorithm is a mechanism that helps Nodes reach consensus in a blockchain network.
On the other hand, consensus algorithms can be interpreted as some policies that drive the consensus of a blockchain. Blockchains are designed as a distributed system network and are not bound to a central authority. However, distributed nodes must agree on the validity of transaction payments. The Consensus algorithm protects the protocol rules that are being followed and protects that all transaction payments take place reliably. At that time, the coins were only completely consumed in one transaction payment.
Distinguish consensus algorithms and protocols
Consensus algorithms and protocols are complementary to each other. However, the meaning of these two concepts is not quite the same. Simply put, protocols are the basic rules of a blockchain. Consensus algorithms are how blockchain enforces those basic rules.
Blockchain is always built on a protocol and system that works on that protocol. Therefore, anyone participating in the Blockchain is required to follow the protocol set out by that blockchain.
The consensus algorithm is the factor that helps the system implement the correct protocol and ensures that everyone involved in the system is also subject to it.

How consensus algorithms work in cryptocurrencies
In cryptocurrency trading, the user’s balance must always be recorded in the database (Blockchain). Intersections (nodes) must always maintain a copy of the same database so that the information does not conflict. Otherwise, that cryptocurrency network will be disrupted.
Public Key Cryptography ensures that users cannot spend each other’s money. However, there needs to be a single source of authentication so that network participants can determine whether the money has been spent or not. To do this, the father of Bitcoin (Satoshi Nakamoto) proposed a system called Proof of Work (PoW), later as the cryptocurrency market grew, developers released more systems (called algorithms) to maintain the stable operation of the Blockchain.
Typical types of consensus algorithms in crypto
Proof of Work (PoW)
PoW is the first consensus algorithm to be successfully applied to blockchain technology. Currently, it is still used by Bitcoin and some other cryptocurrencies such as Ethereum, Litecoin, ZCash, and Monero…
This algorithm requires participants to perform in-depth computational tasks to receive more tests per second. Their calculations are verified by other participants in the network. In other words, the higher the ability to calculate the Hashing function, the easier it is for participants to find solutions for the next blocks.
Hash is a random string of characters and numbers created when a user runs data through a hash function. If you run the same data over and over again, the hash received is always a unique result. But if a small detail is changed in the data, the hash received will be completely different.
However, the PoW algorithm allows miners to have the same opportunity. It ensures that miners can only confirm a new block of transactions and add it to the Blockchain if they receive consensus from the subdivision nodes and provide valid proof of work for Hashing.
PoW makes blockchains like Bitcoin or Ethereum resistant to attacks (such as 51% attacks or majority attacks). Besides, this ability is obtained thanks to the decentralization of the network. The mining process of miners is so expensive that they will not be able to afford to invest individual resources to disrupt the network.
And verifying whether the miner is digging the right block is not necessary. The reason is that even if miners set up a matching hash chain across trillions of combinations and data runs, the network only needs to run their data once. If that hash chain is suitable and accepted then the miner will receive a reward and vice versa.
Proof of Stake (PoS)
In the early days of Bitcoin’s emergence, developers proposed Proof of Stake (PoS) as an optimal solution to replace PoW in 2011. In this system, the concept of mining tools, specialized hardware, or large energy consumption is non-existent. The only thing miners need is a regular PC.
In fact, miners still need to invest in many other things. It’s resources from within (cryptocurrencies). That is, miners need to have a minimum amount of money to qualify for the Stakes. The money was locked in a wallet and the miner couldn’t move it while in stakes. That’s why so far, PoS has only been deployed with small cryptocurrencies.
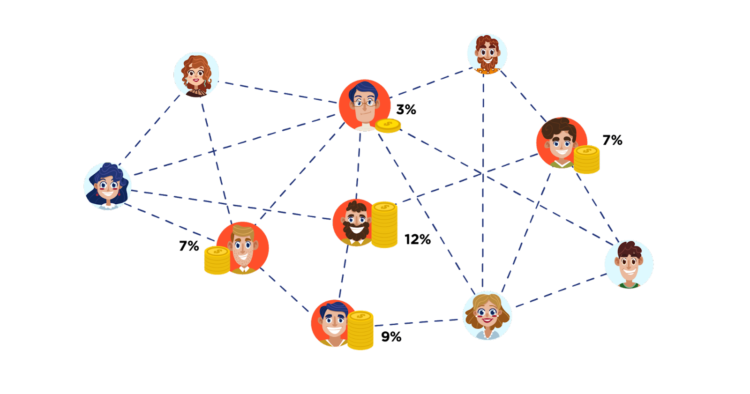
in PoS, the blocks are confirmed according to the share ratio of the participants. The valid validator of each block (minter) is determined by the share ratio of the cryptocurrency rather than by the amount of calculated power allocated. Each PoS consensus algorithm system can perform the algorithm in a variety of ways, as long as the Blockchain is secured by a random fake voting process based on a simple review of the node and how long the coin is locked or deposited (coin age) with a random coefficient.
In the near future, developers will run PoS testing on a large scale (Casper) in a series of upgrades to the Ethereum network (collectively known as Ethereum 2.0).
Delegated Proof of Stake (DPoS)
The way DPoS works is similar to PoS. But instead of making a deposit in advance, the network will implement a voting algorithm for a group of people who are entitled to confirm the transaction.
To ensure fairness and transparency, DPoS will regularly be subject to voting and constantly changing the system to ensure the selected individuals are honest.
In other words, a Blockchain using DPoS will rely on a voting system. In it, the owners of the shares will hand over their work to a third party. That is, they can elect a number of representatives (witnesses) to perform the network security work on their behalf. They have a responsibility to reach a consensus when creating and validating new blocks.
Voting rights correspond to the percentage of users and the voting system varies from project to project. Each representative will present a separate proposal when they ask to receive a vote. The rewards that the representative receives will be divided proportionally among those who voted for them.
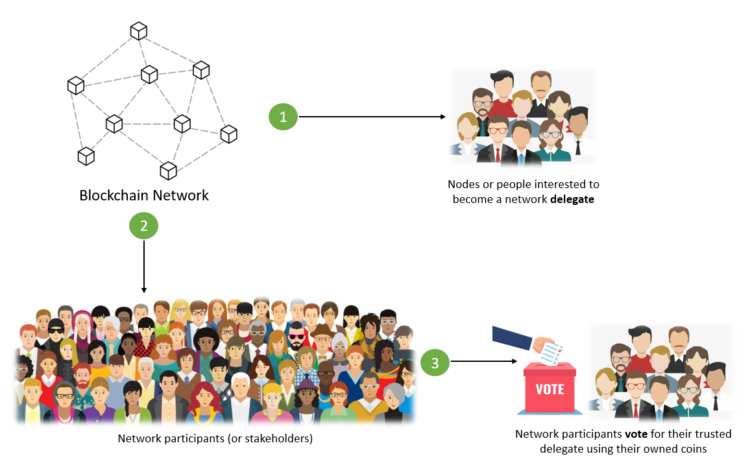
by the DPoS Algorithm to create a voting system that directly depends on the credibility and reputation of the representatives. If one node is elected but is not working effectively and there is misbehavior, it will be quickly expelled and replaced by another node.
In addition to the three typical algorithms mentioned above, networks also use other algorithms to maintain consensus, such as Delayed Proof of Work, Leased Proof of Stake, Proof of Authority, Proof of Burn, Hybrid PoW/ PoS …
See also: Cryptocurrencies And Stocks. What Are The Differences?
Conclusion
Consensus algorithms are important for the operation of decentralized systems. It helps strengthen cryptocurrency (Blockchain) systems and allows developers to run nodes on a decentralized system.