Advertisement
Dusting Attack is a new type of malicious activity in which hackers and scammers try to invade the privacy of Bitcoin and cryptocurrency users by depositing a very small amount of coins into the user’s personal wallet. Many Bitcoin professionals trade in the belief that their anonymity is protected from attempts to hack transactions, but unfortunately, this is not the case!
Definition of Dust

In the language of cryptocurrencies, “dust” refers to a very small amount of coins or tokens – a number so small that one is often overlooked. Take Bitcoin, for example, the smallest unit of this currency is 1 satoshi (0.000000000 BTC) and we can consider a few hundred satoshis as “dust”.

In other words, “dust” is a very small transaction or with a quantity that is not worth sending because it is much smaller than the transaction fee. In cryptocurrency trading, “dust” is also the name that we assign to very small amounts of coins that are “stuck” and cannot be traded.
Most people don’t pay attention to the “dust” in their wallets and rarely worry about its origins. In the past, it was okay not to care about this very small amount of money in your wallet, but with the recent creation of dusting attacks, we can no longer consider it that way.
What is a dusting attack?
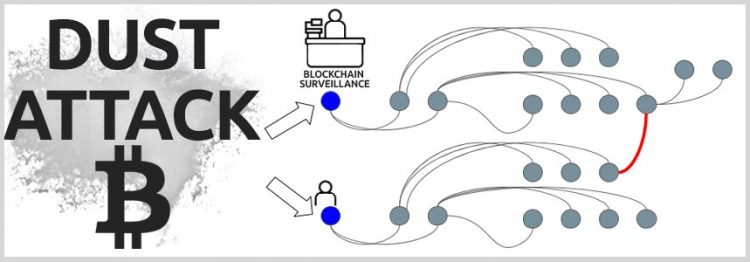
Scammers have recently realized that Bitcoin users don’t pay much attention to the very small amounts of money that appear in their wallets, so they start “dusting” a large number of addresses by sending a few satoshis.
They then begin to track those funds and all the transactions of those wallets that are dusty, allowing them to link to addresses and eventually identify the companies or individuals behind those wallet addresses.
These dusting attacks were originally carried out with Bitcoin but they are also happening with other cryptocurrencies that are operating on an open and transparent blockchain.
At the end of October 2018, samourai wallet developers for Bitcoin announced that some of their users were involved in dusting attacks. The company sent out a warning tweet to its users and instructed how users could protect themselves.
To protect users against dusting attacks, it now provides real-time alerts for dust tracking as well as adding a “Do Not Spend” feature that allows users to mark suspicious items and avoid using them in future transactions.
If the dust is stationary in the wallet, the attacker cannot make the connections they need to “anonymously circumvent” the owner of that wallet or the owner of the address. Samourai wallets already have the function of automatically reporting transactions below the 564 satoshi limit, which provides some level of protection.
See also: What Is Eclipse Attack? The Aftermath Of The Eclipse Attack
Why does Dusting Attack exist?
Cryptocurrency trading is always public, but it’s difficult to know who the owner behind that cryptocurrency is. Hackers can’t rely solely on public wallet addresses to steal cryptocurrencies, they must identify victims in order to continue to apply other attack measures.

The majority of cryptocurrencies today are based on bitcoin’s blockchain prototype, which has a function that allows a private key to create a variety of public wallet addresses. However, hackers can’t rely on public wallet addresses to go back to the private key, they can only go through Dusting Attack to verify which public wallets have the same owner.
How Dusting Attack Works
When hackers deposit cryptocurrencies into a victim’s wallet, the movement path of that cryptocurrency can be easily tracked by the hacker. If they are used for transactions sent to wallets that the hacker already knows the owner of, he can determine who the cryptocurrency belongs to.
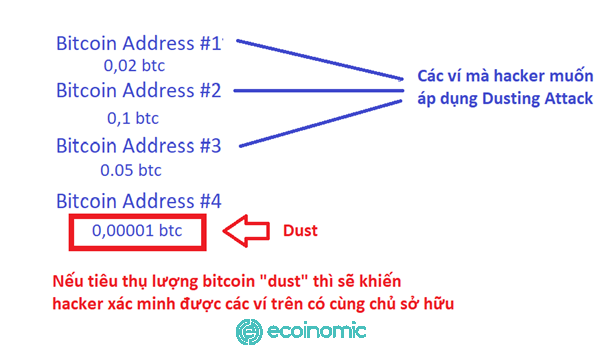
Although the amount of bitcoins in each wallet is displayed independently of each other, they can be consumed collectively in one transaction, which is the mechanism that facilitates dusting attacks to be able to perform.
See also: How To Identify And Avoid Scams On Binance P2P
Ways to Combat Dusting Attack
Dusting Attack prevention is not difficult if we understand their nature and pay attention to precautions, here are simple but effective ways to prevent Dusting Attacks.
- Do not use money sent by hackers: Some wallets have a “do not spend” function to prevent Dusting Attacks like this. If the money is in your wallet, there’s nothing hackers can do about it.
- Use “coin mixers”: This is a special type of software that mixes many different transactions, which makes transaction tracing difficult or impossible to do. You can refer to BestMixer, one of the world’s most popular coin-mixing webs.
- Use anonymous coins such as Dash, Monero, and Zcash. Because they are not publicly traded, Dusting Attack is void.
- P2P trading: Since these types of transactions are usually private, hackers are difficult to track and attack.
- Use a one-time wallet address per transaction: You can create infinite bitcoin wallet addresses, so if it’s not a mandatory situation, create a new wallet address each time you make a transaction. Verifying whose wallet addresses are owned is pointless if you never use them again.