Advertisement
What is an eclipse attack?
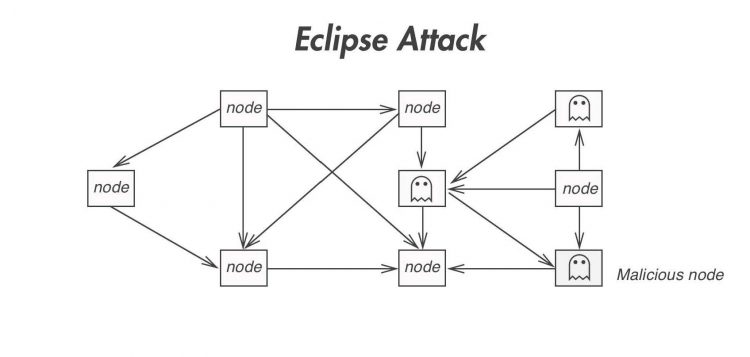
An Eclipse Attack is a relatively simple attack that a harmful agent can deploy to interfere with nodes on the network by isolating a user or a particular node in a Peer-to-Peer (P2P) network. As the name implies, this attack action is intended to obscure participants so that they cannot see the peer-to-peer (P2P) network, causing general disruption or preparing for more sophisticated attacks.
On the surface, obscured attacks may be a bit like the Sybil attacks which are toxic agents that will bring into the network of fake peers. However, their ultimate goal is different. The obscuring attack targets a single node, while the Sybil attack is a network-wide attack designed to undermine the credibility of the protocol.
Furthermore, attackers can start an obscuring attack by building multiple independent nodes that cover the surface through a Sybil attack. Attackers can use the coating maintenance mechanism to carry out an obscuring attack. As a result, protections against Sybil’s attacks failed to prevent obscuring attacks.
The concept was discussed in detail in a 2015 paper titled Hidden Attacks on Bitcoin’s Peer-to-Peer Network, in which researchers from Boston University and Hebrew University presented their research findings from trials that carried out their obscuring attacks, as well as possible countermeasures to combat them.
In an obscured attack, the attacker attempts to redirect the connections to and from the network participant, the target from legitimate nodes to the attacker’s nodes. That way, the target will be blocked from the real network.
Since the target is disconnected from the Blockchain ledger, the isolated node can then be manipulated by the attacker. An eclipse attack can lead to disruption to Block mining as well as confirmation of illegal transactions.
How easily blockchain attacks can be carried out depends on the basic structure of the target blockchain network.
See also: How To Identify And Avoid Scams On Binance P2P
How does an eclipse attack work?
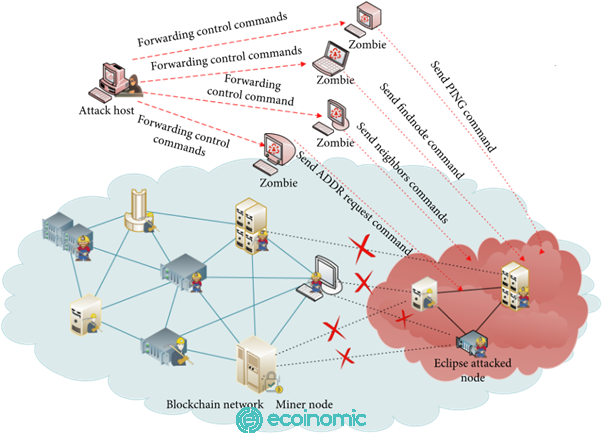
Attackers often use a botnet or virtual network to infiltrate a node and seal it.
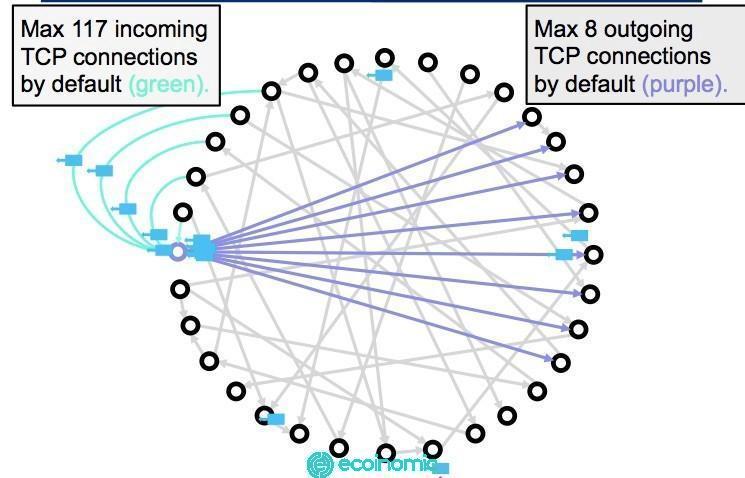
Cryptocurrency Eclipse Attacks can be carried out because nodes in the decentralized network cannot connect simultaneously to other nodes because of bandwidth limitations. Thus, instead, the nodes connect to a limited set of nearby nodes.
Therefore, a malicious agent works to compromise the target user’s connection to a limited group of nodes it connects to. An attacker uses a virtual network or botnet to compromise a node. This network is made up of server nodes and is used to flood a target node with internet protocol (IP) addresses. The target can then synchronize when it reconnects to the Blockchain network.
The attacker will then wait for the target to reconnect to the malicious nodes or use the Distributed Denial of Service (DDoS) attack so that the target is forced to reconnect to the network.
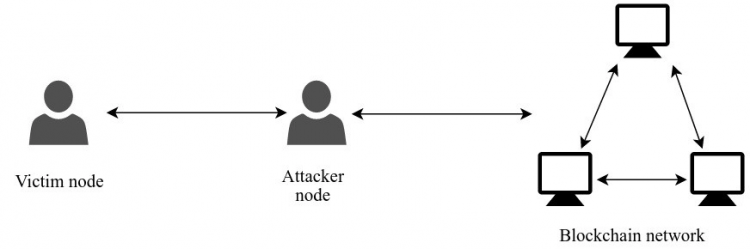
Where a target node is compromised, an attacker can provide the wrong data to it. Often, the victim does not know that the node has been compromised.
The same input of a transaction has been authenticated on the legal network.
See also: What Is A DDoS Attack? DDoS Attacks In The Blockchain
The aftermath of the Eclipse Attack?
Double spending without confirmation
If an individual accepts the transaction without confirmation, they are twice as likely to spend. The transaction may have been transmitted, but if it has not yet been included in a Block, the sender can easily create a new transaction to spend another equivalent amount of money elsewhere. If the new transaction has a higher fee, the miner can disable the previous transaction.
Some businesses and individuals accept these unconfirmed transactions. Let’s say businessman Bob is a seller of high-end car products. He doesn’t know that Alice has obscured his node, and there’s no doubt when she orders a luxury sports car. She made a transaction, then Bob passed it on online. Bob was pleased to see the payment being sent so handed over the car keys and Alice sped off.
Of course, the transaction hasn’t been transmitted to the network yet – Bob only forwards it to Alice’s malicious fake nodes, and these nodes won’t forward to real nodes. While this transaction hangs in limbo, Alice will send a sum of money online (real) to another party or to an address she owns. Even if the initial transaction with Bob is eventually sent to the network, it will be rejected because the second transaction sent that money to another account.
Double spending confirms N
Double spending confirms N is similar to unconfirmed spending but includes more preparation. Many businesses often wait for certain confirmations before marking payments as valid. To deal with this, the attacker must obscure both miners and merchants. Once the attacker has set up an order with the merchant, they pass a trade to the miners (obscured). The transaction is confirmed and included in the Blockchain – but this blockchain is not the chain that the majority of the network observes, as miners have been separated from the chain.
From there, the attacker forwards this version of the Blockchain to the merchant, and this person will ship in the belief that the transaction has been confirmed. When obscured nodes are connected to the real network, then the blockchain they mistakenly believed to be valid will be left behind by the blockchain on which the rest of the network is active (this has some similarities to the 51% attack).
Weakening competitive miners
An obscured node will continue to operate without knowing that they have been separated from the network. Miners will continue to mine blocks according to the rules set out by the protocol, but the added blocks will be removed when they are synchronized with honest peers.
Theoretically, it is possible to use a large-scale obscuration attack on the main miners to facilitate a 51% attack. Therefore, the cost of controlling the majority of Bitcoin’s hashing power is just too high for the most resource-possessing attackers – at speeds of ~80TH/s, the attacker will need more than 40TH/s to perform such an operation.
Assuming this hashing power is distributed between 10 parties (so that each side owns 8Th/s), then the attacker can significantly reduce the requirements for an attack by 51% by removing these parties from the network. If 5 of them are obscured, then 40TH/s will be removed from the race to find the next block and the attacker now only needs more than 20TH/s to gain control.
Obscuring targets can help cause harm in other ways, including manipulating nodes to gain mining rights or racing techniques among miners to find the next block.
How to minimize obscured attacks
With enough IP addresses, an attacker can obscure any node. The simplest method to prevent this from happening is that the operator needs to block incoming connections and only make external connections to specific nodes (such as nodes that have been blacklisted by other colleagues). However, this is not a suitable approach for large scale – if all participants apply these measures, new nodes will not be able to join the network.
The authors suggest several adjustments to the Bitcoin software, some of which have been integrated since the article was published. These adjustments make obscuring attacks more expensive through minor modifications to the codes, such as random selection of new connections and greater address storage.
See also: What Is Ransomware?
Benefits of Eclipse Attack for Network Developers
Developers can familiarize themselves with vulnerabilities in bitcoin nodes that are mined to replace legitimate peer-to-peer addresses with their addresses.
- Technically, when the node selects an IP address from the tried group with a time stamp, it increases the probability of an attacker being selected. This is true even if the attacker owns only a small portion of these addresses. The chances of being selected can also be increased by increasing the time of the attack.
- When a group of addresses is full, an address is deleted at random. If the attacker’s IP is deleted IP, then it can eventually be inserted if it is sent continuously to the node.
As you can see, the attackers can exploit the aforementioned vulnerabilities. However, there are also a number of ways to avoid them:
- The selection of the IP address from the tried table can be done at random. This will reduce the likelihood of the peer being selected as an attacker. If the peer selection is random, then the attacker will not succeed even if he has spent a lot of time on the attack.
- Use the defined method to insert the addresses of colleagues into fixed locations. This will reduce the likelihood of inserting an attacker’s address into a different location after having been kicked out of the address group. A defined approach ensures that repeated insertion of addresses does not add value to an attack.
There are a lot of vulnerabilities in Bitcoin that have been addressed. However, attacks on the blockchain can still be carried out when attackers find other vulnerabilities. This is due to public blockchain networks.
The open-source culture followed by many blockchain organizations could also make way for further security vulnerabilities.