Advertisement
What is Proof-of-authority (PoA)?
Proof of authority (PoA) is an alternative consensus mechanism, based on known and reputable validators to create blocks, thereby providing computing power to the network. It allows transactions to be relatively faster using the Byzantine Fault Tolerance (BFT) algorithm with the identity of a stake.
PoA is a kind of consensus mechanism geared towards private businesses or organizations that want to build their own chains that are essentially closed in nature and do not require the participation of users in general.
This type of consensus mechanism doesn’t cost a lot of resources, but requires validators to protect the integrity of their nodes. It encourages honest action as user identity is a vulnerable factor.
PoA improvements over PoW and PoS
In the context that PoW (Proof-of-Work) is overly ill-worded and expensive, PoS (Proof-of-Stake) algorithms have emerged as one of the popular alternatives to PoW. PoS operates on the assumption that those whose tokens are staked in the network will be encouraged to act in the interests of the network, otherwise, they risk losing their share of tokens.

This is what Proof of Authority aims to improve. The idea behind the PoA algorithm is that instead of focusing on the economic value of the token, network participants will determine their identity.
The PoA Consensus algorithm uses the value of the identifier number, which means that block validators do not create cryptocurrency shares, but instead create their own reputations. Therefore, PoA blockchains are protected by validation nodes that are considered reliable.
In addition, some people think that PoA is a modified PoS that uses identity instead of cryptocurrency. Due to the decentralized nature of most chain networks, PoS is not always suitable for certain businesses and corporations.
In contrast, PoA systems may represent the best solution for private blockchains, as its performance is significantly higher.
How PoA works
The Proof of Authority model is based on a limited number of block validators and this is what makes it an scalable system. Blocks and transactions are checked by pre-approved participants who act as system moderators.
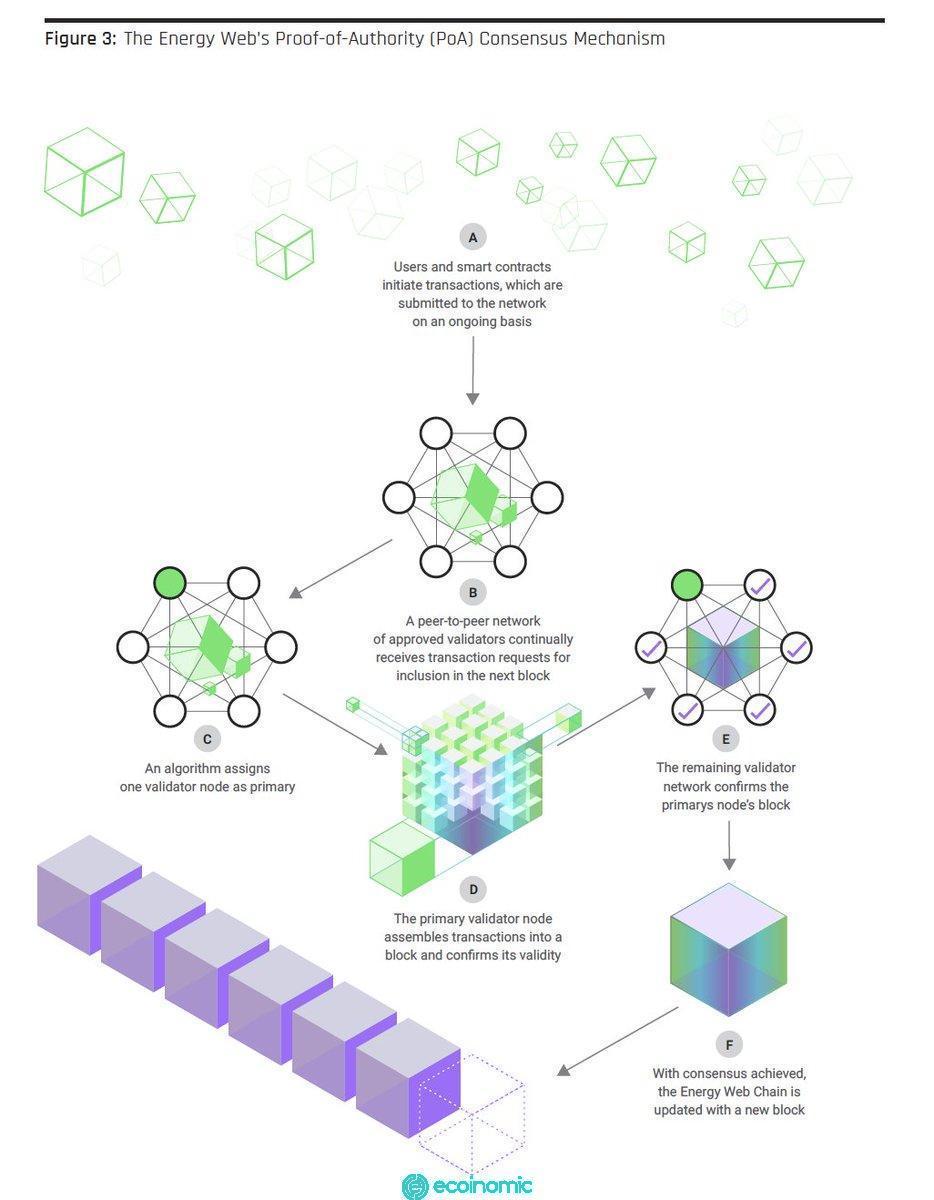
The emulator runs the software to place transactions in blocks. This process is automated and does not require the validator to constantly monitor their computer. However, this requires maintaining the computer (admin site) in good condition.
To be elected as a endorser, the user must comply with three basic conditions:
- Identity must be formally verified online with the ability to cross-check information in the public domain.
- Obtaining the right to be elected as a certifier of the earned blocks and reviews is not easy (for example, a potential notary is necessary to obtain a state notary license).
- There should be full consistency in inspections and procedures to establish authority.
With the PoA algorithm, people have the right to be validators, so they are motivated to maintain the position they receive. To avoid damaging their reputation, the confirmer is motivated to maintain a normal trading process. As a result, most users appreciate their hard-earned role of a validator.
Advantages and disadvantages of PoA
Advantages
- Remove the possibility of an attack because the confirmer has all been tested at the stage of gaining authority and has been verified as reliable.
- It is an energy-saving solution compared to other consensus mechanisms.
- Process transactions quickly
A new block is created in just 5 seconds, the fee is extremely low, and the network ratio can occur horizontally, combining multiple networks into one.
Disadvantages
- With the use of PoA, decentralization is impossible as only a limited group of people can participate in block authentication.
- While PoA can be used in public blockchains, it is often applied in private blockchains that require permission.
- Reputation doesn’t always keep participants from malicious actions. If the reward for cheating is more valuable than authority, the participant may harm the system.