Advertisement
What is 51% attack?
51% Attacks are one of the most common attacks on the blockchain, in which an individual or organization has the majority of control over the network, with such great power, such individuals or organizations can disrupt the network.

The purpose of 51% attack?
Typically the purpose of attacking a 51% Attack on a blockchain is usually for the purpose of double spending fraud, which gives an attacker the right to reverse the transactions it generates and causes double-spending.
If successful, 51% of attacks can:
- Prevent the recording, authentication, or validation of transactions.
- Change the order of transaction processing.
- Reverse existing transactions and then spend twice as much money.
In addition to the negative impact that 51% attacks have on users, they can also affect other miners. By controlling the computing power of the network, 51% attackers can block any mining activity other than themselves. This also poses a significant threat to businesses that rely on blockchain to manage finances and keep transaction records.
And as the number of cryptocurrencies continues to grow, 51% attacks will continue to occur, especially for low-hash rate networks.
It can be seen that a 51% attack may not completely destroy the Blockchain but it can cause great financial and trust damage to users and organizations involved.
See also: What is ransomware?
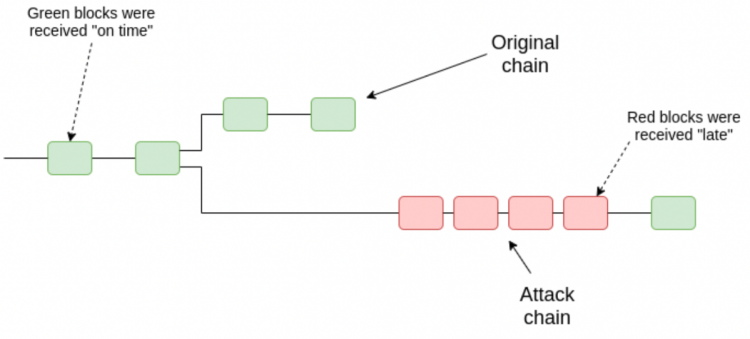
How the attack 51% work?
In the blockchain, blocks record all transactions completed within a certain period of time. For Bitcoin, a new block is created about every 10-15 minutes. Once a block is completed or mined, it cannot be changed because a fraudulent version of the public ledger is quickly detected and rejected by the network’s users.
However, by controlling most of the computing power on the network, an attacker or attacker group can interfere with the production of new blocks. They can prevent miners from completing new blocks, theoretically allowing them to monopolize new blocks and earn all the rewards.
See also: What is eclipse attack? The aftermath of the Eclipse Attack
51% Attack & The Impossible Trio (The Blockchain Trilemma)
Expanding on the issue, 51% of attacks involve an aspect when blockchain design is secure. Blockchain projects today often revolve around three core concepts: decentralization, scalability, and security.
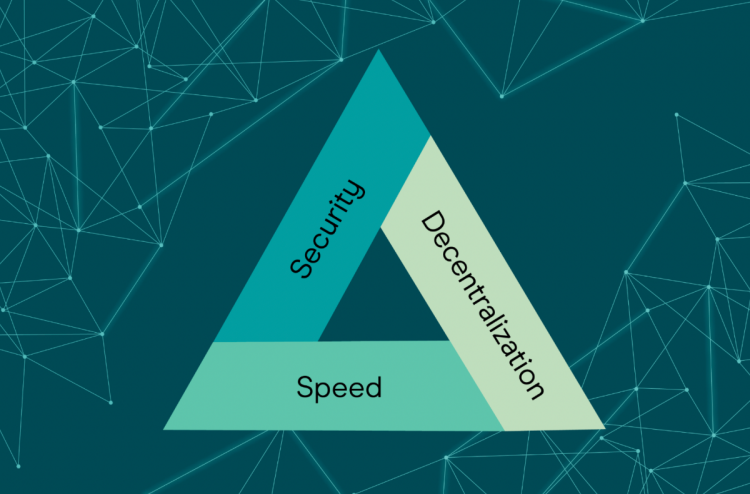
The Trilemma blockchain can be understood as the challenges that developers face in creating an expandable, decentralized, and secure blockchain without compromising any aspect.
Blockchains are often forced to trade-offs that make it impossible for them to achieve all three aspects:
- Decentralized: Creating a blockchain system is not based on the control of an individual or collective.
- Scalable: The blockchain system’s ability to process an increasing number of transactions and can be scaled up.
- Secure: The ability of the Blockchain system to work as expected, protecting itself from attacks, bugs and other unforeseen problems.
For example, the Bitcoin Blockchain, blockchain is considered the most secure in the world but in return the scalability of Bitcoin is very low despite many technical improvements over the years, similar to the case of Ethereum.
In summary, although security is an important aspect of a blockchain, the other two factors also need to be considered, there should be a balance, and should not be biased in any aspect.
In addition, it is important to note that Trilemma is just a model for conceptualizing the various challenges that Blockchain technology faces. There is no evidence that three aspects cannot be achieved at the same time. So far, blockchain teams are still working on different approaches to try to maximize these three core concepts: decentralization, scalability, and security.
See also: How To Identify And Avoid Scams On Binance P2P
Even so, the 51% attack is still only in theory, because when someone can disrupt the fairness and transparency of the network, there will be no more users who trust that network.
Does a person, with the hard work and finances to have the power to dig beyond 51% of the world, want to own a network that no user trusts to use?